
Written By: Staff MRHPx @ B | H aka Rizal (Formerly NeMeSiS_ByTe)
Written On: May 2o11, Between Pasuruan, Malang, Indonesia
Level: Beginner
HACKINTRO
This article I wrote to fulfill the request via email colleagues who curious about the tool called Key Logger. Coincidentally today I'm off work a few days, so I have plenty of time to open some old files stored on Hack Tool My personal server. Fortunately all the source code is still stored properly, so I do not need to rewrite the code this ridiculous. I prefer to use your fingers to play guitar and I dissect animals. Finger curls too much coding is not possible in-rebonding
KEY LOGGER (keystroke logger) DEFINITION
Is a program that runs in the background (Background), recording all the buttons. Key Logger once executed, will automatically hide in the machine to record all data or transmit data directly to the owner of the Key Logger.
Owner Key Logger then reads the data obtained by carefully in hopes of finding the password (Password) or possibly other useful information that can be used as Social Engineering attack. Key Logger can be categorized simply as Thieves Hack Tool Information.For example, Key Logger can reveal the contents of all e-mails written by the victim. Key Logger Program usually found in rootkits and trojans.
Key Logger works for the record (record) all activities of computer users to take data input via keyboard characters used by the user.So if a user typed the word "I" through the keyboard will automatically Key Logger will record it on a LOG file with the data "I".
HACK TOOL KEY LOGGER = Utilities =?
If you have questions, whether it includes a tool Key Logger evil? or a type of software utilities that good? Frankly only you can answer it. Excess humans and other creatures are able to distinguish between good things and where things are not good.
A) Angel Style ..?
Key Logger is often used as a parental advisory (parental control) to supervise the activities of their children during computer use. It is also often used by owners of Internet cafes (cafe), network sharing, and others to monitor user activity. Example: Limiting the adult content (pr0n), parental control against the subject of children on the internet, etc.
B) Evil Style ..?
On the other side of the Key Logger would be very harmful if misused at all, especially for users who become targets of abuse Key Logger tool. All the characters are typed through the keyboard will be recorded properly in the LOG file. Whether it's password, username, bank PIN numbers, accounts FTP / Facebook / etc. From here you can certainly imagine what would happen if you and your computer becomes the target of this crime.
TIPS TO PICK BEST STUFF
Key Logger can be considered quite good and dependable if it meets the following criteria:
A) Its presence is not detected by Antivirus, Anti-Malware and other
You should be proud to have a Key Logger sophisticated and cool, you can just spend your savings to buy a Key Logger software is widely available on the internet. The fact that there is 99% contained Key Logger on the Internet is identified by the Antivirus. Key Logger-priced and well-known even if it is detected by antivirus what can be used?
B) Has the size (Size) is a relatively SMALL <50 KB,
Size DOES Matter, size is important. Key Logger with large size> 50KB (like monster Godzilla Size does not matter) would raise suspicion in the victim's computer. Furthermore, and loading process is definitely longer. It is not effective.
C) PORTABLE and RELIANCE resource (dependency),
Key Logger can be copied and run on different computers without requiring a complicated installation and minimum requirements are convoluted. For example: Programs written using MS Visual Basic largely depends on MSVBVM.DLL, if the victim computer is not there then MSVBVM.DLL Key Logger does not run!
I wonder what the right solution? Anyway, what if asking the victim to download a file MSVBVM.DLL and explain to victims that there is a Key Logger on his computer in your possession that would not be able to run without downloading the file? INSANE solution will certainly make your eyes puffy 3 days 3 nights due to hit the kick of death of the victim who did not receive computer infiltrated by Key Logger you.
What about the attachment solution? Solution MSVBVM.DLL insert in Key Logger also is a solution that INSANE because it will lead to bigger size Key Logger! The correct solution is the optimization code or use a flexible programming language, such as Assembly.
SOME USEFUL APIS
Below I attach to the Microsoft Win32 Programmer's Reference on some of the major API functions are frequently used in programming Key Logger:
Hooks (Reference user32.dll)
Hook is a point in the message-handling mechanism of the Microsoft ® Windows ® where an application can install a subroutine to monitor the traffic of messages in the system and process certain types of messages before reaching the target window procedure.To learn more, please you read the article I entitled "Through the protection of Password and Serial Number on a program with Win32 tricks Hook"
RegisterHotKey (Reference user32.dll)
RegisterHotKey describes a key function to insert a thread.
BOOL RegisterHotKey (
HWND hWnd, / / window to receive hot-key notification
int id, / / hot key identifier of
UINT fsModifiers, / / key-modifier flags
UINT vk / / virtual-key code
);
GetMessage (Reference user32.dll)
Function getMessage take back a message from the calling thread message queue and place them in a defined structure. This function can retrieve both messages associated with the specified window and thread messages posted via PostThreadMessage function. Function retrieve the messages that are within the specified range of the value of the message. GetMessage not take back a message to a window owned by a thread or another application.
BOOL getMessage (
LPMSG lpMsg, / / address of structure with message
HWND hWnd, / / handle of window
UINT wMsgFilterMin, / / first message
UINT wMsgFilterMax / / last message
);
GetKeyboardState (Reference user32.dll)
GetKeyboardState copy function status 256 virtual keys to the specified buffer.
BOOL GetKeyboardState (
PBYTE lpKeyState / / address of array to receive data status
);
GetKeyNameText (Reference user32.dll)
Function GetKeyNameText take back a string that displays the name of a key.
int GetKeyNameText (
LONG lParam, / / second message parameter of the keyboard
LPTSTR lpString, / / address of buffer for key name
int nSize / / maximum length of key-name string length
);
GetKeyState (Reference user32.dll)
Function GetKeyState take back the status of the specified virtual key. Status specifies whether the key up, down, or toggled (on, off ¾ vary each time a key is pressed).
SHORT GetKeyState (
int nVirtKey / / virtual-key code
);
GetAsyncKeyState (Reference user32.dll)
GetAsyncKeyState function determines whether a key is up or down when the function was called, and whether the key is pressed after a previous call to GetAsyncKeyState.
SHORT GetAsyncKeyState (
int vKey / / virtual-key code
);
PROOF OF CONCEPT
MRHPx Key Logger v1.8 (PUBLIC VERSION) is probably the world's smallest Key Logger, with a size only a width of 10.5 KB (10.752 bytes) without compression!
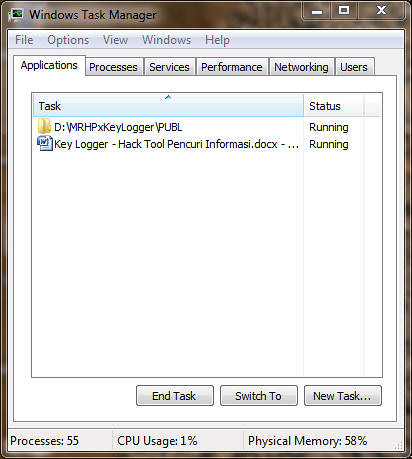
Screenshot 1. Task Manager Applications Tab
Assembly programming language I use 32 bits (instead of 16 bits Assembly outdated) for coding this Key Logger. Assembly 32 bits equal to C / C + +, Delphi, VB, other advantages are faster. Remember, Key Logger is not visible in Task Manager Applications tab, do not have a GUI (User Interface) much less colorful as the party flag at election time. My concept is to create Key Logger with a minimalist but powerful resource DEWA tub ARROW SWISS ARMY KNIFE such other rootkits running in the background ..

Screenshot 2. LOG file
Next please you to type anything using the hardware keyboard or virtual keyboard. Any application that you use to type data will be stored as well in the LOG file separately. LOG file will store data on a regular basis every time a new application is run. To read the LOG files you do not need to exit the application because I was not setting the permissions limit user files. For those of you who want to know more about some other features that you please read the file "BACA_AKU.txt" are included. To exit the Key Logger simultaneously please press the "CTRL + ALT + P" on your keyboard.
FINAL NOTES
Key Logger is very dangerous if used as an instrument of crime. At first glance it looks trivial, because in general the data stored in the LOG file is quite random (NOTE: some Shareware Key Logger LOG files on the internet have a very chaotic because it is made randomly by the coder BEGO and Matre). But what happens if the data LOG file is used as a bruteforce dictionary with the help of tools like John the Ripper and the other? To obtain the victim's username and password information, the data initially random and trivial will become effective and the dictionary can be used as an access log in just minutes.
Another example is if you are a teacher or a lecturer and a student who was a hacker (cracker I mean), it is not likely your students will always get the best value when you insert your exams because students Key Logger on a laptop that you use to develop a test script . Without the need to study hard, just read the script a test that has been stolen by the Key Logger, your students will look to match Mr. Habibie's cleverness in doing the exam the next day
Horrible is not it? But do not worry because there is a simple and effective way to prevent your computer is infiltrated by Key Logger is to enable the User Account Control (UAC), check the Registry Autorun and Startup Windows Service and check the applications running in the background and looks suspicious in your computer.
For other methods, such as heuristic detection antivirus, firewall and so on, knowing I have it less effective. Since hackers do not require a long time to anticipate Antivirus detection is almost always based on the signature algorithm (Trademark virus). Just by changing a few lines of code contained in the source code, then the Hack Tool will not be detected again by the Antivirus.Effectiveness of the signature contained in the antivirus databases was released for Hack Tool is not a PRIVATE PUBLIC VERSION VERSION. Another method as a quick and easy alternative is often chosen by the hackers to bypass antivirus detection is by using astub or stub Commercial Protector UD. Hopefully this article useful and can help you secure yourself from cyber crime.
No comments:
Post a Comment